- Home
- Insights
Real-world insights
Explore ideas, perspectives & trends shaping CX
Get the latest business news, research and consumer trends, plus thought leadership and in-depth analysis of individual industry sectors and business challenges.
7 proven tips for remote and hybrid working models
The debate surrounding remote, hybrid and fully on-site work models…
What is Net Promoter Score and how does it work?
For over two decades, the Net Promoter Score (NPS) has…
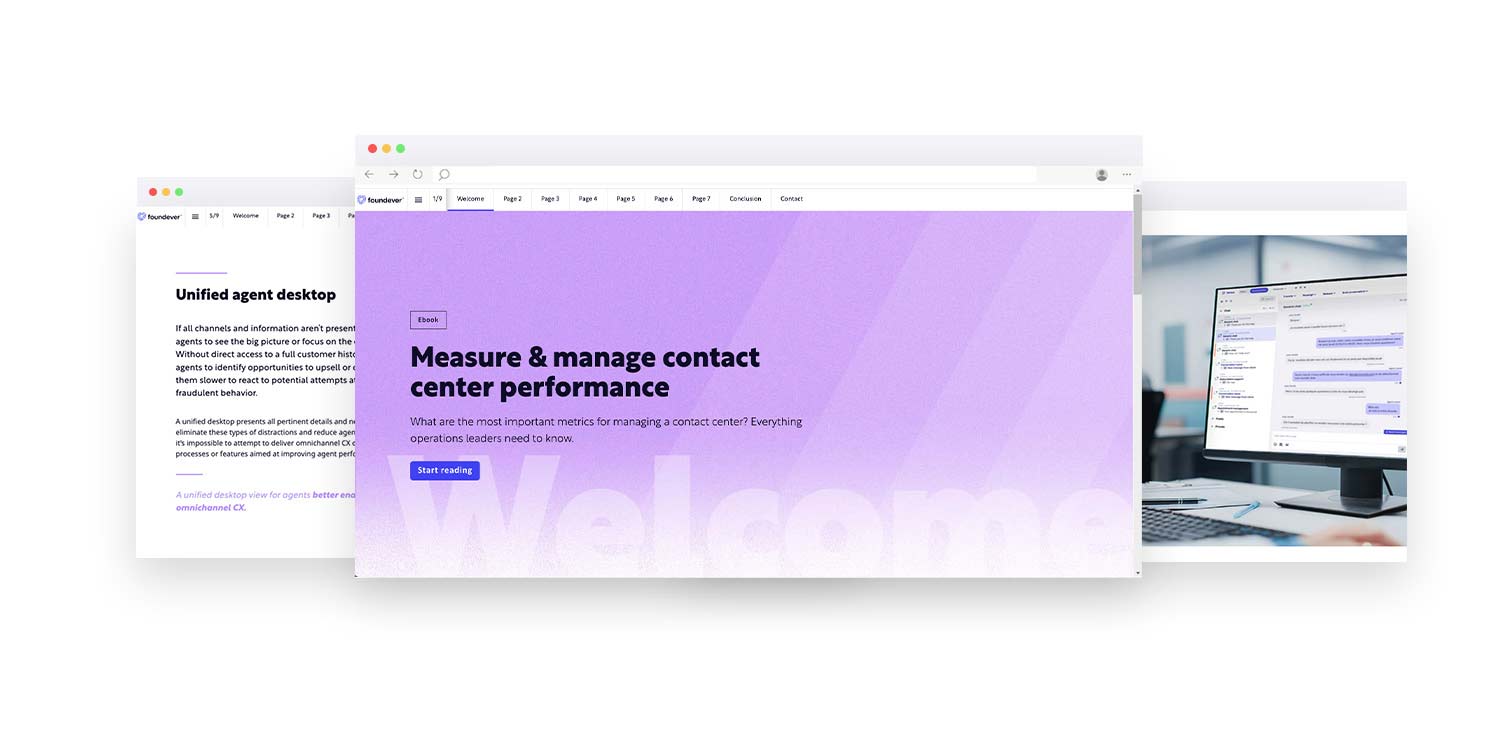
Measure & manage contact center performance
What are the most important metrics for managing a contact center?
Foundever™ location spotlight: Cairo, Egypt
As Foundever™ expands hubs across the globe in culturally rich…
Foundever.org: 5 principles of the CX for Good movement
Foundever.org (a private operating foundation) is committed to upskilling talent…
The 5 biggest business process outsourcing myths
Business process outsourcing (BPO) isn’t about cutting costs or sacrificing…
A leading fintech company streamlines operations while reducing cost to serve
The key to the project’s success was clear planning and…
Luxury EV brand uses CX to accelerate sales
How do you create a buzz, drive sales and provide…
A hospitality innovator uses multilingual hubs to achieve an outstanding NPS and cut employee attrition
Our comprehensive solution utilized strategically located multilingual support hubs for…